Earlier in April, the U.S. Nationwide Institute of Requirements and Expertise (“NIST”) printed Particular Publication (“SP”) 800-61, Incident Response Suggestions and Issues for Cybersecurity Threat Administration, Revision 3 (“NIST SP 800-61”). NIST SP 800-61 Revision 3 (“Revision 3”) is a big change, because it not solely represents the primary replace of the doc since 2012, but additionally now maps the doc’s suggestions and concerns for incident response to the six capabilities outlined within the recently-updated NIST Cybersecurity Framework 2.0—Govern, Determine, Defend, Detect, Reply, and Get well. Because of this, Revision 3 consists of important new suggestions and steerage for incident response, and entities ought to take into account reviewing and updating their incident response plans and procedures to include these suggestions, significantly if an entity has aligned its cybersecurity program with the NIST Cybersecurity Framework or used the prior variations of NIST SP 800-61 as a foundation for current incident response plans or procedures.
NIST SP 800-61, which was first printed in 2008 and final up to date in 2012, is designed to help organizations with cybersecurity incident response and cybersecurity threat administration. In Revision 3, NIST “[p]erformed a full rewrite of the earlier content material to enhance readability and usefulness and to take away outdated materials,” and “[s]hifted the main focus of the doc from tips on detecting, analyzing, prioritizing, and dealing with incidents to suggestions and concerns for incorporating cybersecurity incident response concerns all through a corporation’s cybersecurity threat administration actions.”
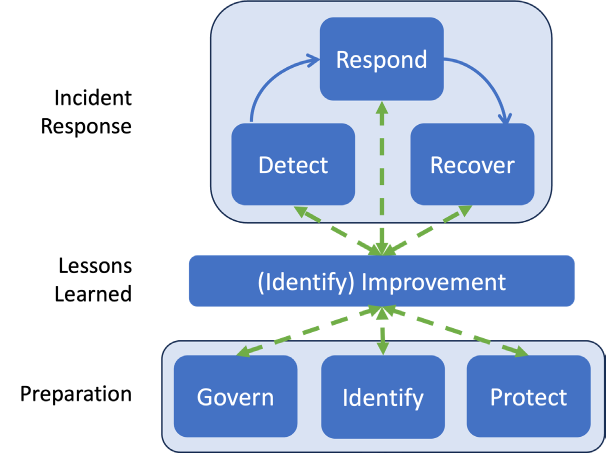
Determine 1. Revision 3 Incident response life cycle mannequin primarily based on CSF 2.0 Capabilities
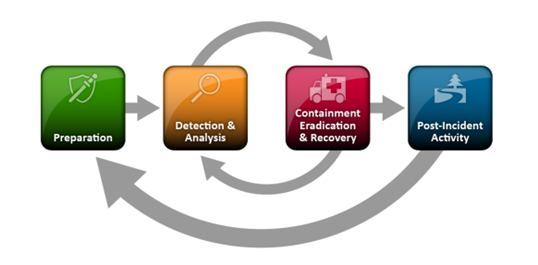
Determine 2. Earlier incident response life cycle mannequin.
Revision 3 consists of a number of important updates, together with:
- Mapping On to NIST Cybersecurity Framework 2.0 – Because the prior Revision 2 of NIST 800-61 was printed in 2012, earlier than the publication of the NIST Cybersecurity Framework 1.0 in 2014, Revision 2 doesn’t map to the NIST Cybersecurity Framework. For the primary time, NIST 800-61 Revision 3 “makes use of the [Cybersecurity Framework] 2.0 Capabilities, Classes, and Subcategories to arrange its suggestions, concerns, and different data concerning incident response.” In mild of this replace, entities may also take into account revisiting and updating their very own incident response insurance policies and procedures to mirror current modifications in Revision 3 and Cybersecurity Framework 2.0.
- Life Cycle Mannequin Restructure – Revision 3 proposes a brand new Incident Response Life Cycle Mannequin that, in line with NIST, seeks to handle a modified incident response panorama the place incidents happen extra often and are more and more complicated and dynamic. Because of this, the brand new Life Cycle Mannequin in Revision 3 acknowledges that incident preparation actions, which fall underneath Govern, Determine, and Defend within the Cybersecurity Framework, usually are not restricted to incident response however mirror broader, ongoing cybersecurity threat administration and incident preparation actions. Subsequently, these Cybersecurity Framework capabilities at the moment are damaged out into the underside degree, or basis, of the Life Cycle Mannequin, labeled “Preparation”. Against this, actions particular to incident response—which fall underneath the capabilities Detect, Reply, and Get well—make up the highest degree, titled “Incident Response”. As well as, the brand new Life Cycle Mannequin features a center part, titled “Classes Discovered” to emphasise the significance of steady enchancment (tied to the Determine Operate throughout the Cybersecurity Framework). In updating the life cycle mannequin, NIST acknowledges that each group varies, and consequently, the suitable life cycle framework or mannequin may differ by group (e.g., “bigger and extra technology-dependent organizations are more likely to profit extra from utilizing a framework or mannequin emphasizing steady enchancment”). In the end, NIST emphasizes that regardless of the mannequin used, incident response must be built-in as a part of a corporation’s broader cybersecurity threat administration actions.
- Cybersecurity Framework Suggestions – Revision 3 features a important variety of suggestions and substantive concerns in two new in depth tables that explicitly map to the capabilities, classes, and subcategories within the Cybersecurity Framework. One desk addresses the capabilities associated to preparation and classes realized (Govern, Determine, and Defend), and the opposite addresses capabilities extra particularly associated to incident response (Detect, Reply, and Get well). As just a few examples, a number of the key suggestions from these tables which might be marked as excessive precedence are: 1) the synchronization of enterprise continuity plans with incident response plans since incidents have the potential to undermine enterprise continuity; 2) the implementation of steady monitoring “for unauthorized exercise, deviations from anticipated exercise, and modifications in safety posture,” which ought to contain monitoring of networks and community companies, {hardware} and software program, personnel exercise and know-how utilization, and exterior service supplier actions; and three) consideration for use and rely on technological options to filter giant, probably antagonistic, occasion datasets right down to a subset that’s appropriate for human viewing and evaluation.
- Steady Enchancment – One other level of emphasis for Revision 3 is a better concentrate on flexibility and a continued cycle of studying as a part of ongoing incident response preparation and cybersecurity threat administration. Whereas most entities have included classes realized on the conclusion of their incident response processes, Revision 3 means that classes realized can be a steady course of informing preparation, the incident response, in addition to restoration to “sustain with fashionable threats.” Along with after motion evaluations following an incident, entities can implement this suggestion by means of periodic tabletop workout routines in addition to integrating learnings from periodic threat assessments or evaluations of their broader cybersecurity program into their incident response procedures.
Lastly, Revision 3 acknowledges that particulars of incident response finest practices “change so typically and differ a lot throughout applied sciences, environments, and organizations, it [therefore] is now not possible to seize and keep . . . data in a single static publication.” As an alternative, given the fast tempo of incident response, NIST established a brand new Incident Response web site the place NIST will host hyperlinks to incident response assets. NIST mentioned that “[b]y transferring hyperlinks from [SP 800-61] to an internet site, NIST can replace and broaden them as wanted with out having to launch a brand new model of [SP 800-61].”