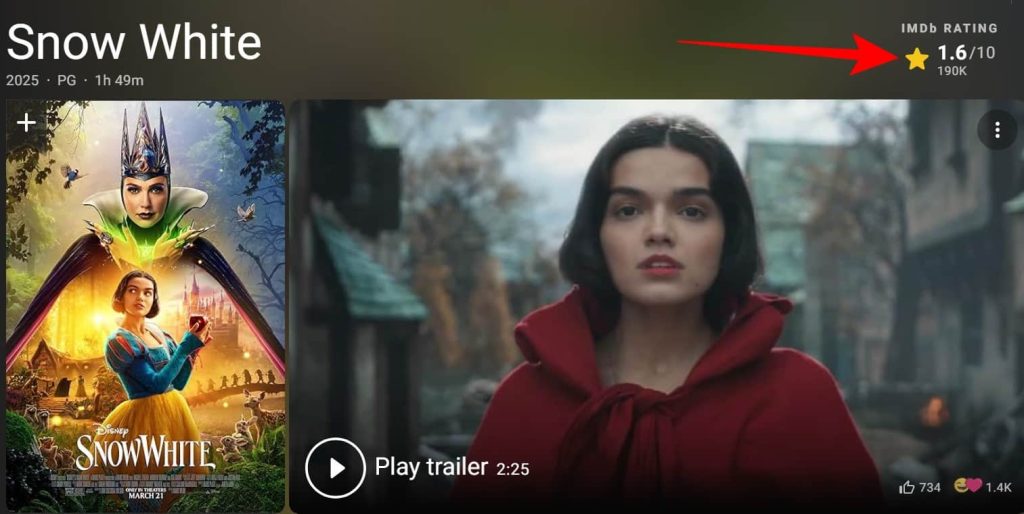
Disney’s newest Snow White film, with a 1.6/10 IMDb ranking, isn’t simply the most important flop the corporate has ever launched. It’s such a humiliation that the film isn’t even obtainable on Disney’s personal streaming platform, Disney+.
Based on cybersecurity researchers at Veriti, scammers are exploiting the state of affairs by providing pirated variations of Snow White, particularly concentrating on torrent customers and tricking them into downloading malware.
The Lure of a Pirated Obtain
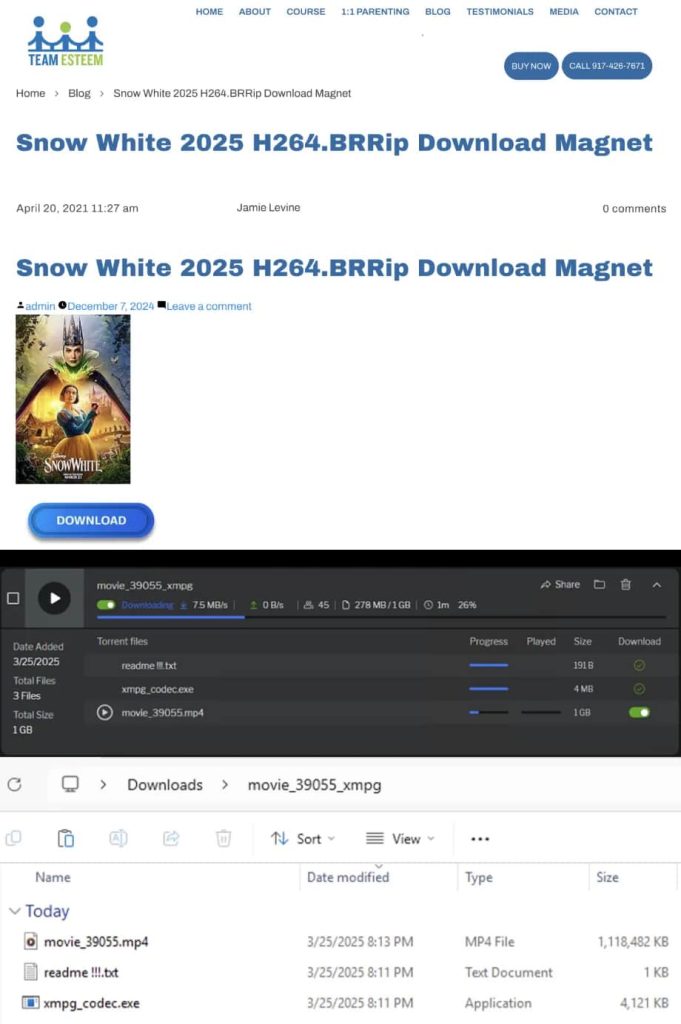
On March twentieth, what initially seemed to be a authentic weblog submit on the web site “TeamEsteem” (teamesteemmethodcom) provided a pirated model of the 2025 Snow White film. The submit supplied a magnet torrent hyperlink that appeared secure however was truly a lure. Researchers recognized the torrent file as a malicious marketing campaign designed to compromise customers’ units.
Based on the corporate’s weblog submit shared with Hackread.com, the torrent hyperlink led to a package deal of three recordsdata. Whereas it may need appeared like a normal film obtain, it was something however. Veriti discovered that 45 individuals have been already sharing or “seeding” the file, which might embrace each unsuspecting victims and attackers working to unfold the lure sooner.
A Pretend Codec That “Spells” Hassle
When customers downloaded the torrent, they didn’t get a film. As a substitute, they bought a bundle of recordsdata, together with a README doc and a suspicious file named “xmph_codec.exe.” The README claimed the codec file was essential to play the film, a typical trick used within the early days of on-line piracy to idiot customers into putting in malicious software program.
Nonetheless, on this case, working the “codec” file triggered a series of malicious actions on the person’s machine, together with the next:
- Disables Safety: It shuts down Home windows Defender and different built-in protections, leaving the machine extensive open to extra assaults.
- Installs Malware: The file was flagged as malicious by 50 out of 73 safety instruments on VirusTotal, a well-liked platform for analyzing suspicious recordsdata.
- Drops Extra Threats: It quietly provides further dangerous recordsdata to the system, setting the stage for additional harm.
- Installs TOR Browser: It downloads and installs the TOR browser, a software usually used to entry the Darkish Internet, with out the person’s data.
- Connects to the Darkish Internet: The malware communicates with a hidden server on the Darkish Internet (utilizing a .onion deal with), making it laborious for safety instruments to trace or block it.
In brief, what seemed like a free film exposes customers to information theft or presumably ransomware.
What’s The Reference to TeamEsteem?
TeamEsteemMethod.com is the official web site of Group Esteem, LLC, a US-based group based by Jamie Levine, devoted to aiding dad and mom, colleges, and educators in addressing varied childhood challenges.
Veriti’s group believes the attackers behind this marketing campaign managed to get their malicious weblog submit onto the TeamEsteem web site in one in all two methods: both by exploiting a vulnerability within the outdated model of the Yoast search engine optimization plugin or through the use of stolen admin credentials to entry the web site.
The vulnerability in query is CVE-2023-40680, discovered within the outdated model of the Yoast search engine optimization plugin, a well-liked search engine optimization software utilized by over 10 million WordPress web sites. Alternatively, the attackers might have logged into the positioning utilizing stolen admin credentials to submit the pretend weblog entry themselves.
Both manner, the attackers used the positioning as a medium to trick customers into downloading their malware, banking on the hype round Snow White to attract in victims.
Not The First Time
This isn’t the primary time cybercriminals have used pirated films as bait, and it gained’t be the final. Excessive-profile releases like Snow White are prime targets as a result of they appeal to big curiosity, particularly when authorized choices are restricted. With no streaming launch on platforms like Disney+, many followers flip to torrent websites, hoping to save cash or time. However as this marketing campaign reveals, there’s no such factor as a “free lunch.”
Prior to now, attackers have exploited the recognition of films like John Wick 3, Contagion, Black Widow, Joker, Ford v Ferrari, Pirates of the Caribbean, and lots of others to distribute malware and ransomware.
The excellent news? You’ll be able to nonetheless keep away from falling into traps by avoiding piracy, being cautious with malicious torrents, retaining your anti-malware up to date to detect the newest threats, and utilizing frequent sense.









![The № 1 Factor Gross sales Professionals Neglect Whereas Pitching [Deal Killer Alert!] | by Aldric Chen | The Startup | Might, 2025](https://www.theautonewspaper.com/wp-content/uploads/2025/05/1c5new8BRNfvmO54EeEQLsA-120x86.jpeg)


